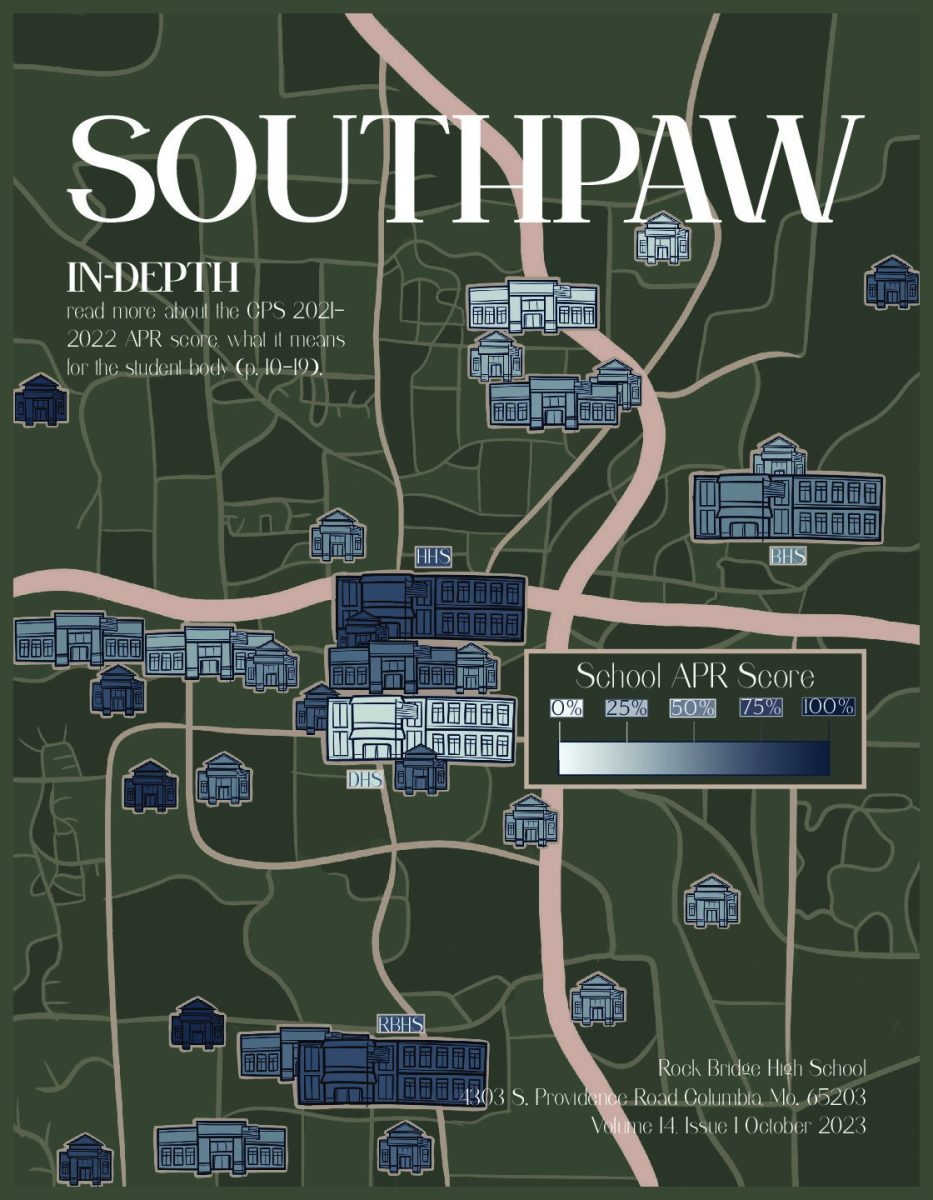
infographic by Sarah Poor
An important phrase when talking about servers, or areas in the tech space where information is stored, is “encrypted files” or “encrypted information.” Programmers use encryption to store valuable information, like usernames and passwords relevant to their websites, in secure areas. This gives hackers a harder time when trying to gather that information.
OpenSSL is an open-source project, meaning it was made by a group of people and given to the public to use for free, and more than half of the Internet uses it. An example of a service whose server is OpenSSL is Amazon Web Services, which is a massive program used by millions of people worldwide.
Programmers implemented Heartbeat, a feature in OpenSSL, to add a test function to help servers test their websites. The test was a response in the form of a heartbeat, as in the server would respond with what was put in directly. This built-in feature of OpenSSL is the area in the program where the glitch was found.
This glitch, called Heartbleed, came a little less than one year ago, when OpenSSL got updated to version 1.0.1. It took almost a year to realize the glitch existed. By the time Heartbleed was found, everyone had already adapted to the new system, so it gave hackers a huge advantage.
Heartbleed did what it sounds like; rather than responding in a heartbeat, the server would bleed out information that was not relevant to the test, and this information contained passwords and usernames and other necessary data used for websites.
Salahodeen Alani, a product manager at a consumer finance startup in Silicon Valley that had to quickly patch their servers to remove the heartbleed vulnerability, works with computer code and is knowledgeable in computer programming.
The glitch “lets you sniff, or look at small blocks of web traffic in encrypted channels,” Alani said in an email interview. “This allows people to find the encryption keys, which means they could read any and all traffic [a server] has ever sent, including usernames and passwords.”
Imagine a programmer testing his server by asking it to respond with the word he gives to the server. The programmer types in the word, and the server takes the data in and attempts to respond. However, in order for it to know how to respond, the programmer must also specify the length of that word. The server then responds with the correct word. This is what Heartbeat is; Heartbleed, then, is a malfunction in the Heartbeat feature. In the Heartbleed situation, someone would ask the server to respond with a word, but he would specify a longer length than presented. The server would spit out the word along with all the information following it in the server’s world, which would display information entered into the server recently.
“I think [Heartbleed] was really bad and it could have been easily used to get information from people,” junior David Asplund said. “I personally didn’t change my passwords because I don’t have important information on any of my accounts, but if I was banking I definitely would have [changed my passwords].”
Once found, programmers upgraded OpenSSL to version 1.0.1.g, in which the bug no longer existed. Even after the update, it is definitely advised to change all passwords for certain websites that were affected by the glitch, such as Google, Yahoo and Amazon, among many others.
This glitch sets a precedent with computer programming; mistakes can always happen, especially in the fragile environment of the Internet, a place where all information associated with banks, credit cards, jobs and much more is stored.
Even without this bug, it is always a good idea to regularly change passwords on important services, like email and shopping sites, because even though it may not seem like it, the Internet is widely open to hackers at any time, and accidental programming errors like this can always occur. As the saying goes, it’s better to be safe than sorry.
By Abdul-Rahman Abdul-Kafi